KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A massive phishing campaign pretending to be a Subway order confirmation is underway distributing the notorious TrickBot malware.
TrickBot is a trojan malware infection commonly distributed through phishing campaigns or installed by other malware.
When installed, TrickBot performs a variety of malicious behavior, including spreading through a network, stealing saved credentials in browsers, stealing Active Directory Services databases, stealing cookies and OpenSSH keys, stealing RDP, VNC, and PuTTY Credentials, and much more.
Even worse, TrickBot partners with ransomware operators, such as Ryuk, to access a compromised network to deploy ransomware.
Today, BleepingComputer was alerted to a new phishing campaign pretending to be Subway order confirmations targeting people from the United Kingdom.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
What is concerning about these phishing emails is that they include the user’s first name, and some users are reporting they are being sent to emails only used for Subway. This attack may indicate a data breach at Subway UK that allowed the threat actors to gain access to customer’s names and email addresses.
In an statement to BleeingComputer, Subway stated that they are investigating a disruption to their system.
“We are aware of some disruption to our email systems and understand some of our guests have received an unauthorised email. We are currently investigating the matter and apologise for any inconvenience. As soon as we have more information, we will be in touch, until then, as a precautionary measure, we advise guests delete the email,” Subway told BleepingComputer in a statement
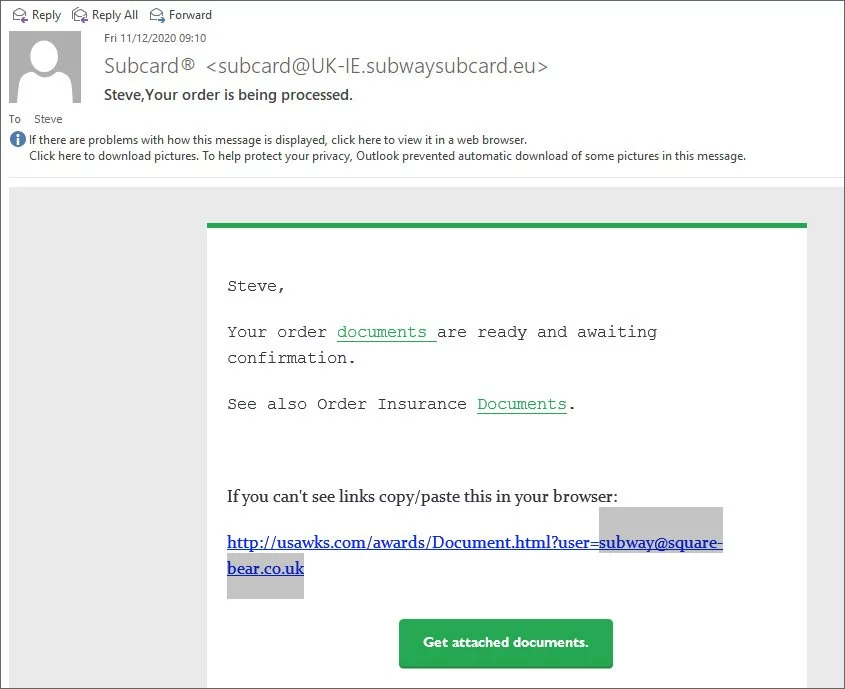
The Subway phishing emails are using email subjects such as “Your order is being processed” and “We’ve received your order,” and state that it is from Subcard ([email protected]), as shown below.
These emails are odd as they tell the user to click on various links as their “order documents are ready and awaiting confirmation.” That seems like a lot of work to order a sandwich.
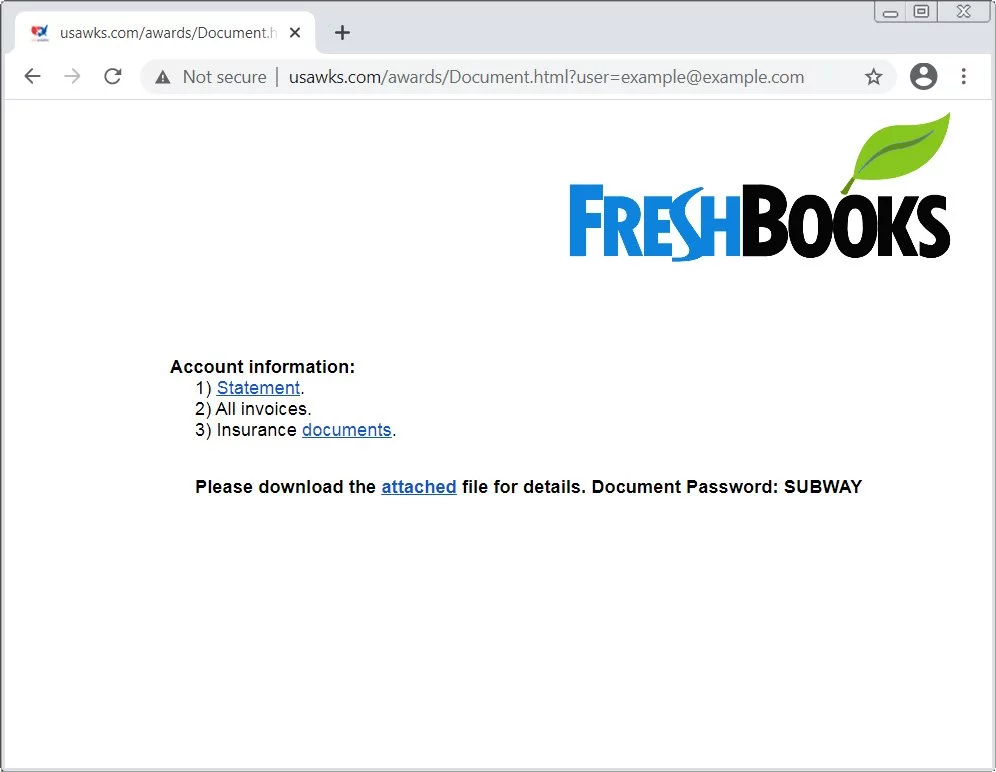
These links lead to various hacked websites that will bring you to a ‘FreshBooks’ phishing page when clicked on. Clicking on any of the links on this landing page will download an Excel spreadsheet.
Depending on the variant of the phishing email you received, the Excel spreadsheet may be password protected. Once the password is entered, a fake and malicious DocuSign phishing attachment will be displayed. This document states that there is a problem previewing the document, and you need to click on ‘Enable Editing’ and ‘Enable Content’ to view it.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
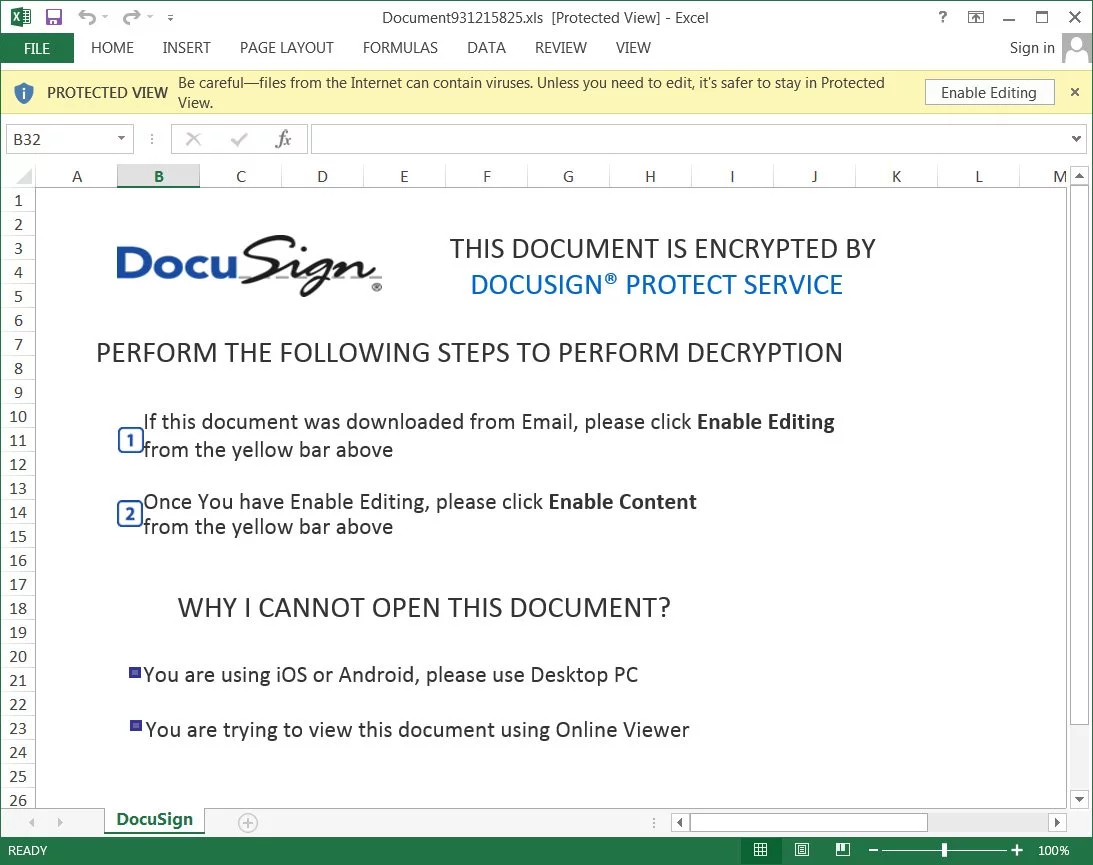
If a recipient enables the content, it will also enable malicious macros embedded in the Excel spreadsheet that download and install the latest version of the TrickBot malware.
The downloaded TrickBot malware is a DLL [VirusTotal] that will be injected into the legitimate Windows wermgr.exe (Windows Problem Reporting) executable directly from memory using code from the ‘MemoryModule‘ project.
By running within Wermgr.exe, it may be to evade detection by security software and will look like a legitimate process in Task Manager.
If you have received this email and accidentally downloaded and opened the malicious document, make sure you perform a thorough scan of your computer using antivirus software and clean anything that is found.