KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







K-12 educational institutions in the U.S. are being targeted by malicious actors for extortion, data theft, and general disruption of normal activity. The trend will continue through the 2020/2021 academic year.
The alert comes from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) based on reports from K-12 institutions incurring cyberattacks.
In a joint advisory today, the three government agencies are warning that ransomware, malware delivery, and DDoS attacks are the main threats for K-12 educational institutions.
Ransomware attacks in the education sector have increased at the beginning of the school year, with cybercriminals stealing data and threatening to leak it unless the ransom was paid (just like in the case of targets in the business and industry sector).
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
“In August and September, 57% of ransomware incidents reported to the MS-ISAC involved K-12 schools, compared to 28% of all reported ransomware incidents from January through July”
– FBI, CISA, MS-ISAC joint advisory
Based on data aggregated from both open-source and third-party incident reports, the most prevalent ransomware families affecting K-12 institutions between January and September were Ryuk, Maze, Nefilim, AKO, and REvil.
Non-targeted attacks against this sector delivered multiple malware strains, the most common ones being Shalyer, ZeuS, Agent Tesla, NanoCore, and cryptocurrency miners.
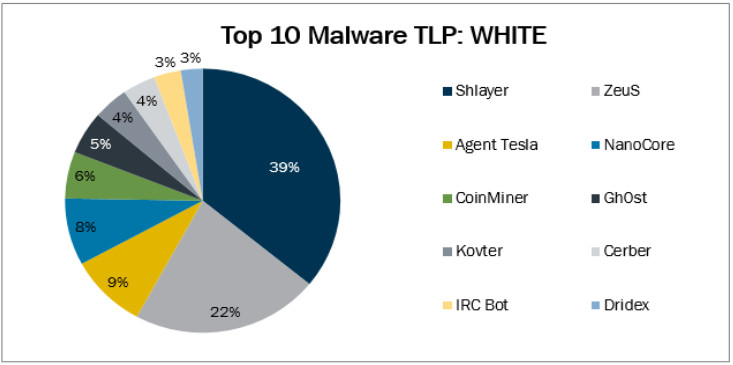
Shlayer malware for macOS that continues to evolve. Recently, its authors came up with a trick that bypasses Apple’s scanning for malicious code and code-signing issues in software running on macOS 10.15 (Catalina) and above.
Last year, Kaspersky security solutions for Mac detected Shlayer on 1 in 10 systems and this malware strain accounted for 30% of all detections on Apple computers.
ZeuS is a long-standing trojan (first detected in 2007) that has turned into an information stealer (banking/financial information, credentials).
Agent Tesla and NanoCore, are off-the-shelf information stealer and remote access tool, both a common tool in business email compromise (BEC) fraud.
Coinminers, while not malicious, can slow down systems and drive up energy due to increased power required by the mining activity.
The alert from the FBI, CISA, and MS-ISAC also warns of DDoS incidents causing disruptions of normal operations in the K-12 sector.
This echoes a report from Check Point in mid-September about a surge of these attacks against education and academic institutions.
The three U.S. agencies say that the reason behind the increased incidence of these attacks is the availability of DDoS-for-hire services that enable “any motivated malicious cyber actor conduct disruptive attacks regardless of experience level.”
Activity disruptions were also caused by uninvited users attending video classroom sessions to verbally harass students and teachers, display unsuited material (violent, pornographic content), and doxing participants.
This was possible by accessing meetings from links exposed to the public or to outside users, or by tricking hosts into accepting their participation by using student names.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
The FBI, CISA, and MS-ISAC also highlight risks related to social engineering carried through phishing, domain typosquatting, against students, parents, faculty, IT personnel, or other people involved in distance learning.
Cybercriminals could use these attacks to obtain personally identifiable information, passwords, to lure users to malicious websites, or deliver malware.
Defending against most attacks requires little effort. In most cases, applying software updates promptly, correcting misconfiguration, using strong, unique passwords, enabling multi-factor authentication, and disabling ports that are not needed should keep most cybercriminals at bay.
The government alert provides a comprehensive set of actions that K-12 educational institutions should take, along with Snort signatures that CISA created to detect and protect against attacks with observed malware; the rules should complement other defense methods.