KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Proof-of-concept exploit code and full details on a Windows Kerberos security bypass vulnerability have been published earlier this week by Jake Karnes, the NetSPI security consultant and penetration tester who reported the security bug to Microsoft.
The security bug tracked as CVE-2020-17049 and patched by Microsoft during November 2020’s Patch Tuesday can be exploited in what the researcher has named as Kerberos Bronze Bit attacks.
Karnes provides a high-level summary of the vulnerability and details on how attackers can exploit it to compromised vulnerable Windows systems.
He has also published a low-level overview of the security bug with additional information on the Kerberos protocol, as well as practical exploit scenarios and details about how to implement and use Kerberos Bronze Bit attacks.
The release of the proof-of-concept exploit code by Karnes on Tuesday was prompted by Microsoft publishing the security updates needed to fully mitigate CVE-2020-17049 on vulnerable servers.
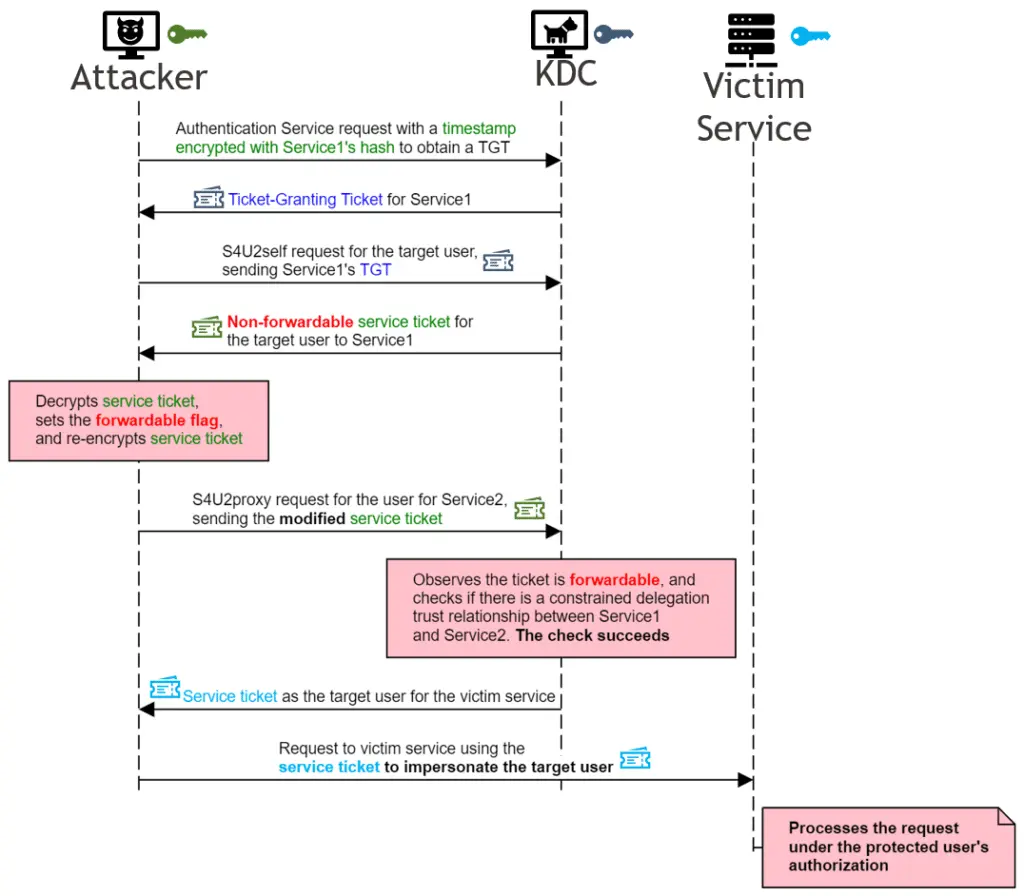
As explained by Karnes, the Kerberos Bronze Bit attack abuses the S4U2self and S4U2proxy protocols Microsoft added as Active Directory Kerberos protocol extensions.
The S4U2self protocol is used in the attack to obtain the service ticket of the targeted user, a ticket later manipulated “by ensuring its forwardable flag is set (flipping the “Forwardable” bit to 1).”
“The tampered service ticket is then used in the S4U2proxy protocol to obtain a service ticket for the targeted user to the targeted service,” Karnes says.
“With this final service ticket in hand, the attacker can impersonate the targeted user, send requests to the targeted service, and the requests will be processed under the targeted user’s authority.”
The CVE-2020-17049 exploit is designed to bypass Kerberos delegation protection allowing attackers to escalate privileges, impersonate targeted users, and move laterally on compromised environments.
“Because this is accomplished by flipping a single bit, and in the spirit of the Golden Ticket and Silver Ticket attacks, I’ve dubbed this the Bronze Bit attack,” Karnes added.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
Microsoft is addressing the Bronze Bit vulnerability in a two-phase staged rollout, with the initial deployment phase having started on December 8th (requiring admins to manually enable enforcement) and an automatic enforcement phase starting on February 9th, 2021.
The initial security updates released by Microsoft in November led to Kerberos authentication problems on affected enterprise domain controllers where patches were deployed.
These issues included authentication problems when using S4U scenarios and cross-realm referrals failures on Windows and non-Windows devices for Kerberos referral tickets.
A week after the CVE-2020-17049 security updates were issued, Microsoft also released out-of-band optional updates to fix the Kerberos authentication issues on all impacted Windows devices.
Microsoft also published patching guidance the same week, with additional info on how to fully mitigate Bronze Bit.
To fully address CVE-2020-17049, Microsoft has now released additional security updates on December 2020 Patch Tuesday that provide “fixes for all known issues originally introduced by the November 10, 2020 security updates.”
Also Read: Letter of Consent MOM: Getting the Details Right
“Microsoft strongly recommends that customers running any of these versions of Windows Server install the updates and then follow the steps outlined in https://support.microsoft.com/help/4598347 to enable full protection on domain controller servers,” the company added in an update to the CVE-2020-17049 security advisory added on December 8th.
As part of the December 2020 Patch Tuesday, Microsoft has also issued security updates to address a separate Kerberos security feature bypass vulnerability (CVE-2020-16996) impacting multiple Windows Server versions in a two-phase staged rollout.