KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







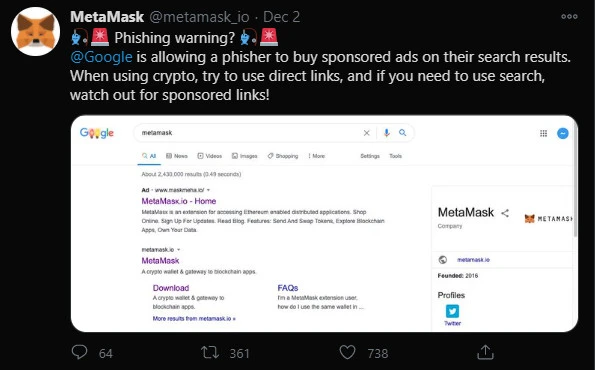
Over the past week, users of the MetaMask cryptocurrency wallet have been losing funds to a phishing scam that lured potential victims through Google search ads.
MetaMask has a community of more than one million users. The site offers an Ethereum cryptocurrency wallet in the browser via a browser extension that lets distributed applications read from the blockchain.
When installing the legitimate extension, you can either import an existing wallet or create a new one along with the secret seed phrase that allows access to the wallet.
Although it is unclear how many MetaMask users fell for the scam, some say they ended up with empty wallets after clicking on a fraudulent search ad being promoted as the MetaMask site.
The phishing/ad scam is still active, with a new domain constantly being promoted via Google search ads.
On Wednesday, MetaMask alerted its community of the scam and recommended the use of direct links to the legitimate metamask.io URL and to stay away from sponsored ads.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
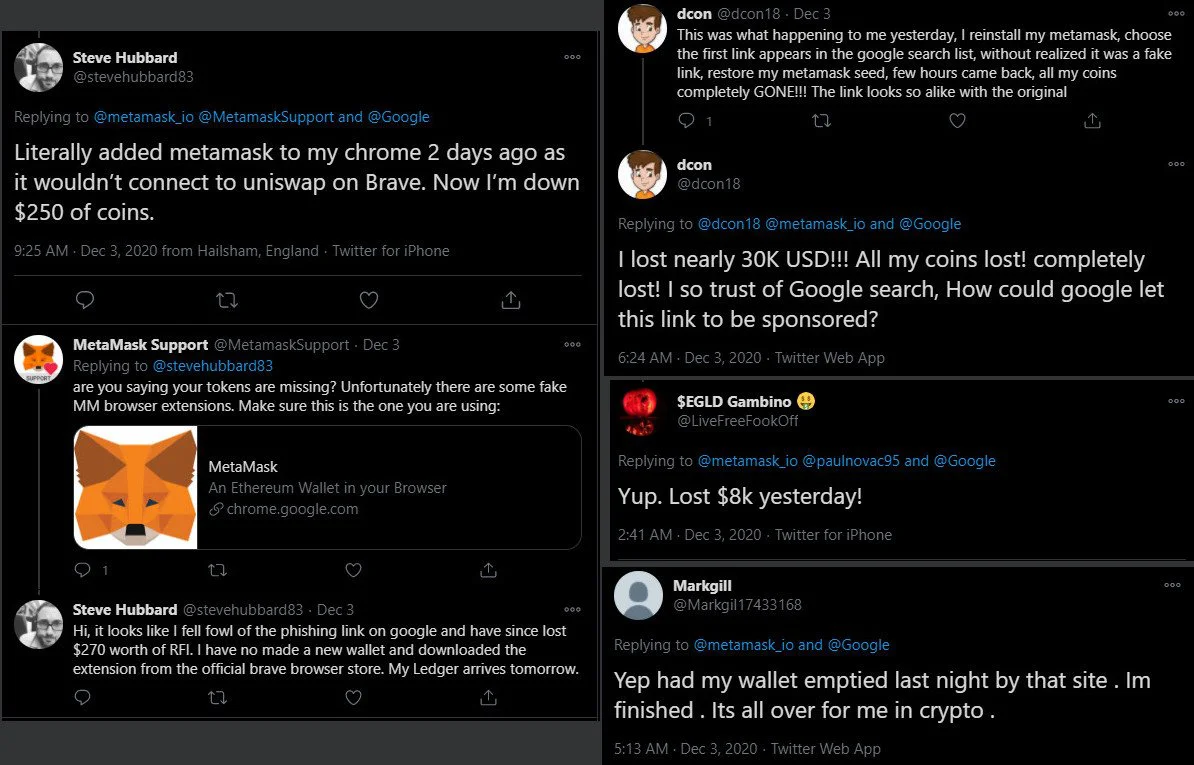
The warning came too late for some users, though, as some users reported losses of tens of thousands of U.S. dollars.
Complaints started pouring in this week, all stories describing the same scenario: the money was gone after trying to install the MetaMask browser extension.
It was determined that the users were going to a fake MetaMask phishing page through Google ads. Once on the page, they are prompted to install the extension, which will give them an option to either import an existing wallet or create a new one.
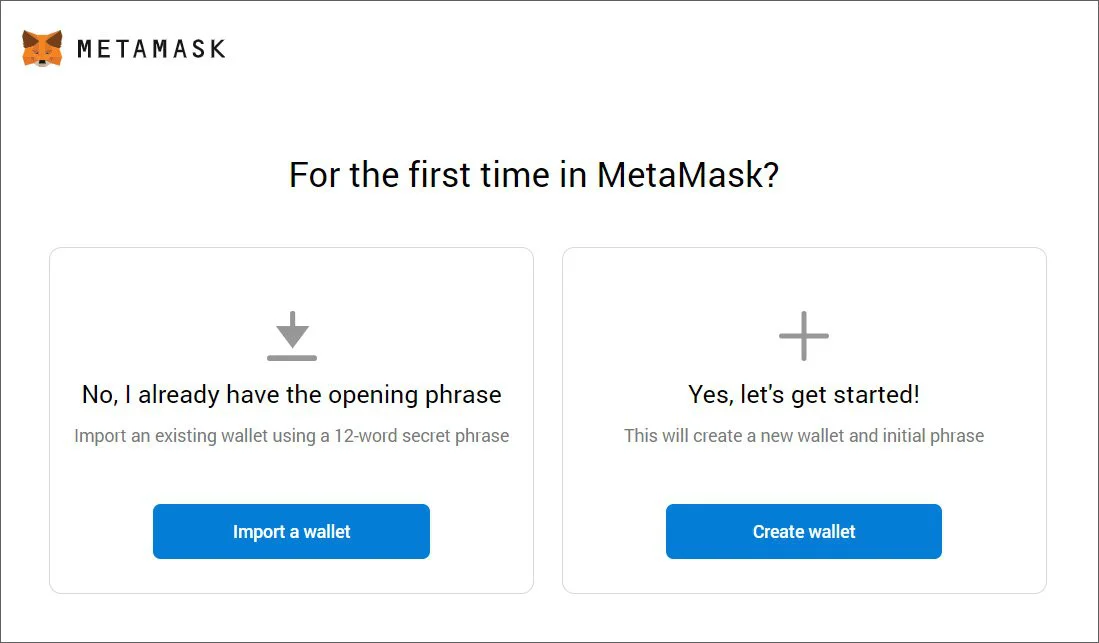
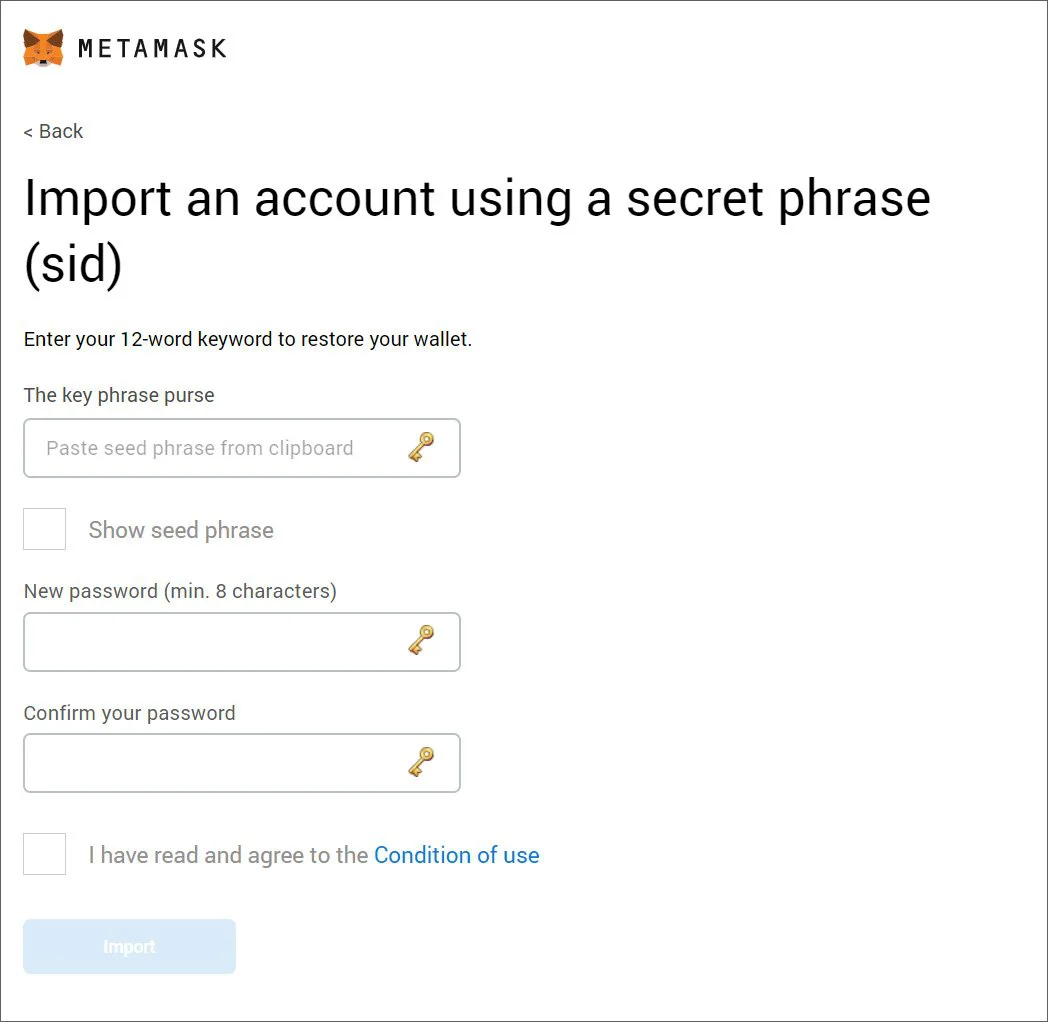
If they click on the ‘Create Wallet’ button, they are brought to the real MetaMask.io site as there are no cryptocurrency to steal. However, if they click on the ‘Import a wallet’ option, they will be asked to enter the key phrase of their existing wallet, which is then sent to the attacker.
As soon as the scammer got the seed phrase, they proceeded to empty the victims’ wallets. In replies to MetaMask’s warning on Twitter, one user said they were robbed of nearly $30,000.
The scammers purchased Google ads to target users searching for MetaMask in the Google search engine. These ads led to a fraudulent domain impersonating the cryptocurrency service.
They registered multiple domains for the scam, which is currently ongoing, as seen in the screenshot below taken by BleepingComputer:

The domain maskmefa[.]io is currently promoted in search ads when looking for MetaMask on Google. The spelling of the service in the title ad should be a red flag, but most users are likely to miss this (note the Russian “к” and space before the top-level domain). A whois lookup on Domaintools shows that it was registered only yesterday.
Blockchain forensics company CipherTrace in a post this week mentions three other domains used for the scam:
The first two are ten and nine days old, respectively, while the third was registered yesterday. All were registered through the same registrar, NameCheap.
Users landing on the fraudulent sites would have difficulty spotting the fraud because it looks almost identical to the legitimate MetaMask page. Even if they check the domain in the address bar, there is a high chance of falling for the trick.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
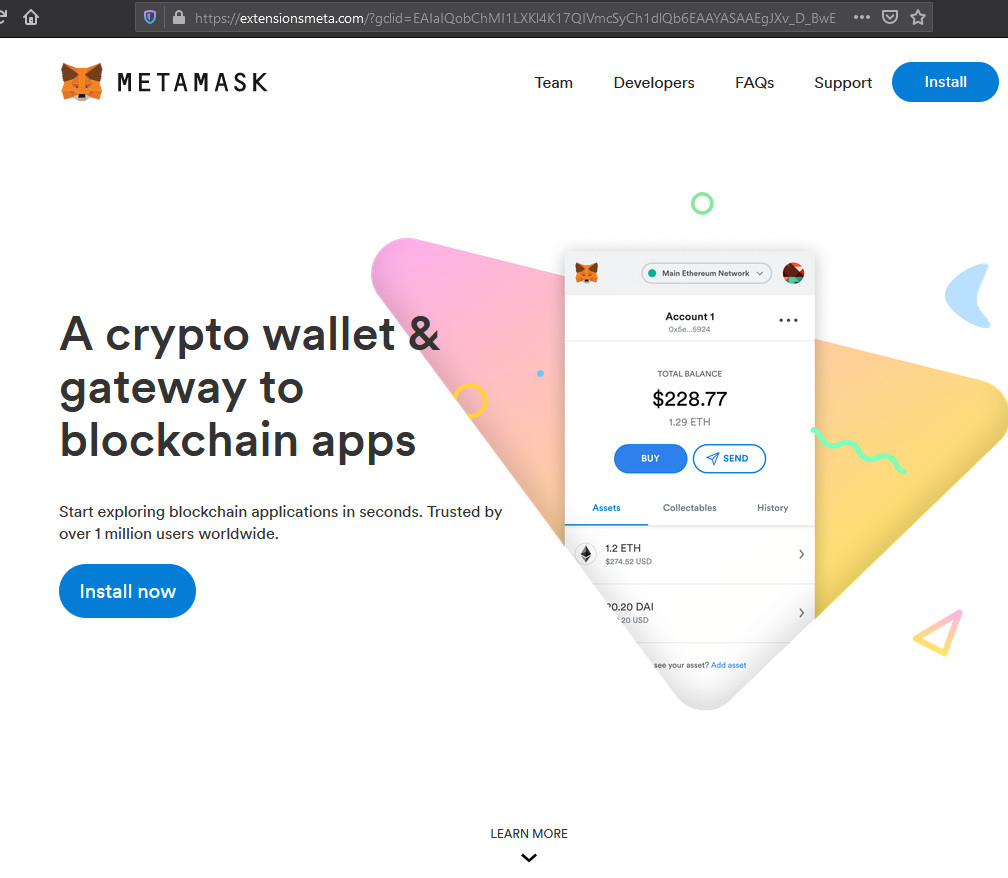 Fake MetaMask site Fake MetaMask site |  Legitimate MetaMask site Legitimate MetaMask site |
The only difference between the original MetaMask site and the fake one is unnoticeable for most users (the writing on the button for getting the extension).
The only difference between the original MetaMask site and the fake one is unnoticeable for most users (the writing on the button for getting the extension).
Scams and malware attacks increase in frequency during the holiday season when consumers spend more enticed by discounts or special offers and are more easily distracted.
Paying extra attention to download sources reduces the chance of becoming a victim. MetaMask’s advice to access resources from direct, official links (e.g., company accounts on LinkedIn, Twitter, Facebook) and avoiding redirects from third parties (e.g., URLs in messages) is a good way to not fall for a scam.