KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ransomware negotiation firm Coveware has placed the DarkSide operation on an internal restricted list after the threat actors announced plans to host infrastructure in Iran.
When the DarkSide ransomware operation encrypts a network, their affiliates steal unencrypted files, which they threaten to release if a ransom is not paid.
This double-extortion strategy is always under attack by law enforcement and security firms who try to disrupt or take down ransomware data leak sites where stolen files are published.
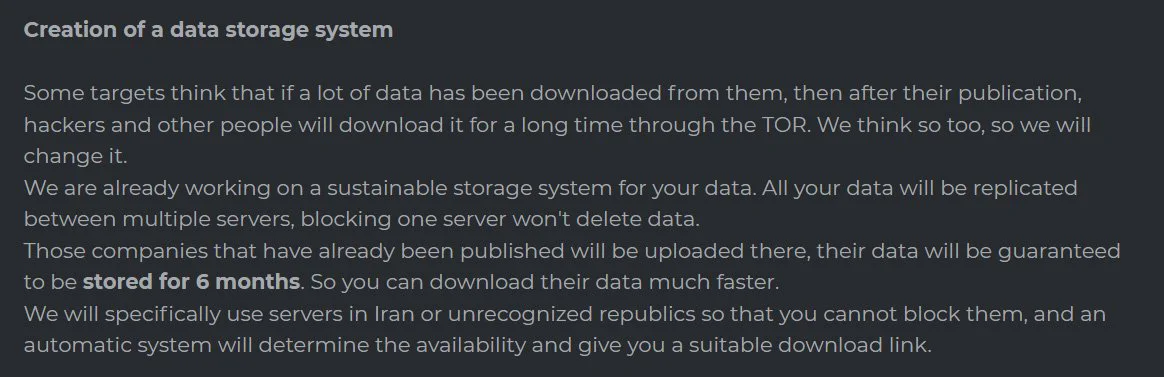
To prevent their data leak service from being taken down, the DarkSide gang announced this week that they are building a distributed and sustainable storage system in Iran and other “unrecognized republics.” With this system, if one server is taken down, the data will still remain and be available on the other servers.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
In October, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) issued an advisory that warned ransomware negotiators and U.S. businesses that paying ransom could lead to sanction violations and fines.
As examples of sanctioned hacking groups that are known to deal with ransomware, the advisory mentioned:
In addition to sanctions against these hacking groups, the U.S. government has sanctions against Iran.
As ransom payments to DarkSide could be used to pay Iranian hosting providers for this new data leak system, Coveware has placed DarkSide ransomware on an internal restricted list and will no longer facilitate ransom payments with them.
“DarkSide’s own TOR site announces the intent to use infrastructure hosted within Iran, a sanctioned nexus. The purpose of this infrastructure is to store data stolen from victims of ransom attacks. It is probable that a portion of the proceeds from any prospective ransom payment to DarkSide would be used to pay services providers within Iran. Accordingly, we have placed DarkSide on our restricted list,” Coveware CEO Bill Siegel told BleepingComputer.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
BleepingComputer has learned that an email sent to partners explains that this is Coveware’s decision and not part of any U.S. policy.
With that said, the hosting of DarkSide servers in Iran will be an additional hurdle businesses must face when determining if they will pay a ransom.