KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







There were not many known large ransomware attacks this week, but we have seen ransomware operations evolving their tactics to extort their victims further.
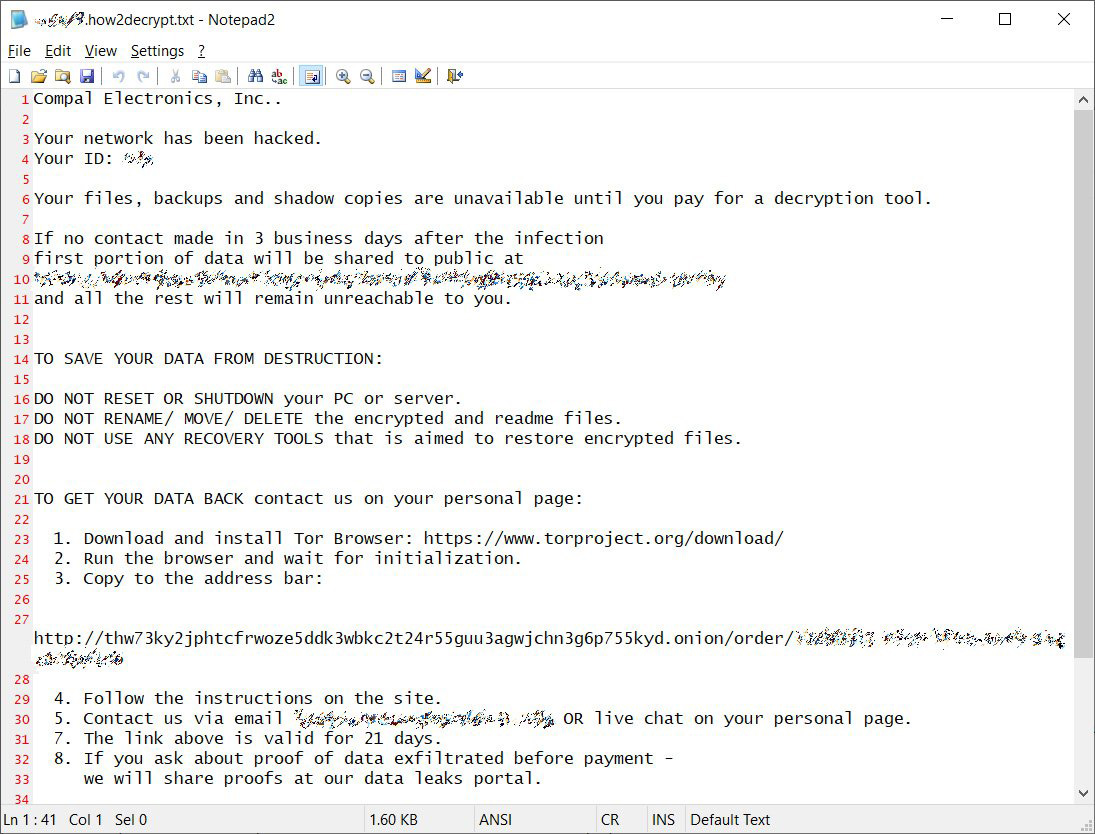
The largest attack this week was against Tawainese laptop maker Compal, who was hit by DoppelPaymer. The threat actors are demanding $17 million to receive a decryptor and not to leak stolen files.
Ransomware operations have also begun new tactics this week to pressure their victims into paying a ransom.
After their attack on Campari, Ragnar Locker hacked a Facebook advertiser’s account to run Facebook ads promoting their attack and threatening to release more data. Their strategy is to apply as much pressure as they can on the victim through public awareness in the hopes it will force them to pay the ransom.
Another new tactic announced by DarkSide is their plans to create a fault-tolerant distributed storage service based out of Iran or other “unrecognized republics.” Their goal is to use this storage as a platform to leak victim’s data for six months, and due to its distributed nature, if one server is shut down by law enforcement, the other servers will still be able to leak the data.
Otherwise, this week has been mostly new variants of existing ransomware families.
Contributors and those who provided new ransomware information and stories this week include: @serghei, @malwrhunterteam, @jorntvdw, @PolarToffee, @VK_Intel, @Ionut_Ilascu, @demonslay335, @LawrenceAbrams, @struppigel, @FourOctets, @malwareforme, @Seifreed, @DanielGallagher, @fwosar, @BleepinComputer, @LukasZobal, @siri_urz, @JAMESWT_MHT, @Unit42_Intel, @briankrebs, @Kangxiaopao, @MsftSecIntel, @campuscodi, @Intel_by_KELA, @briankrebs, and @IntelAdvanced.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
One hacker group that is targeting high-revenue companies with Ryuk ransomware received $34 million from one victim in exchange for the decryption key that unlocked their computers.
While researching these malware families, we found that there were several consistencies between Vatet, PyXie and Defray777 that strongly suggest that all three malware families were created, and are currently maintained by, the same financially motivated threat group.
Ransomware operators are using malicious fake ads for Microsoft Teams updates to infect systems with backdoors that deployed Cobalt Strike to compromise the rest of the network.
Michael Gillespie found a new STOP ransomware variant that appends the .agho extension to encrypted files.
Lukáš Zobal found the new Dusk 2 ransomware variant that appends the .DUSK extension to encrypted files and drops a ransom note named README.txt.
Taiwanese laptop maker Compal Electronics suffered a DoppelPaymer ransomware attack over the weekend, with the attackers demanding an almost $17 million ransom.
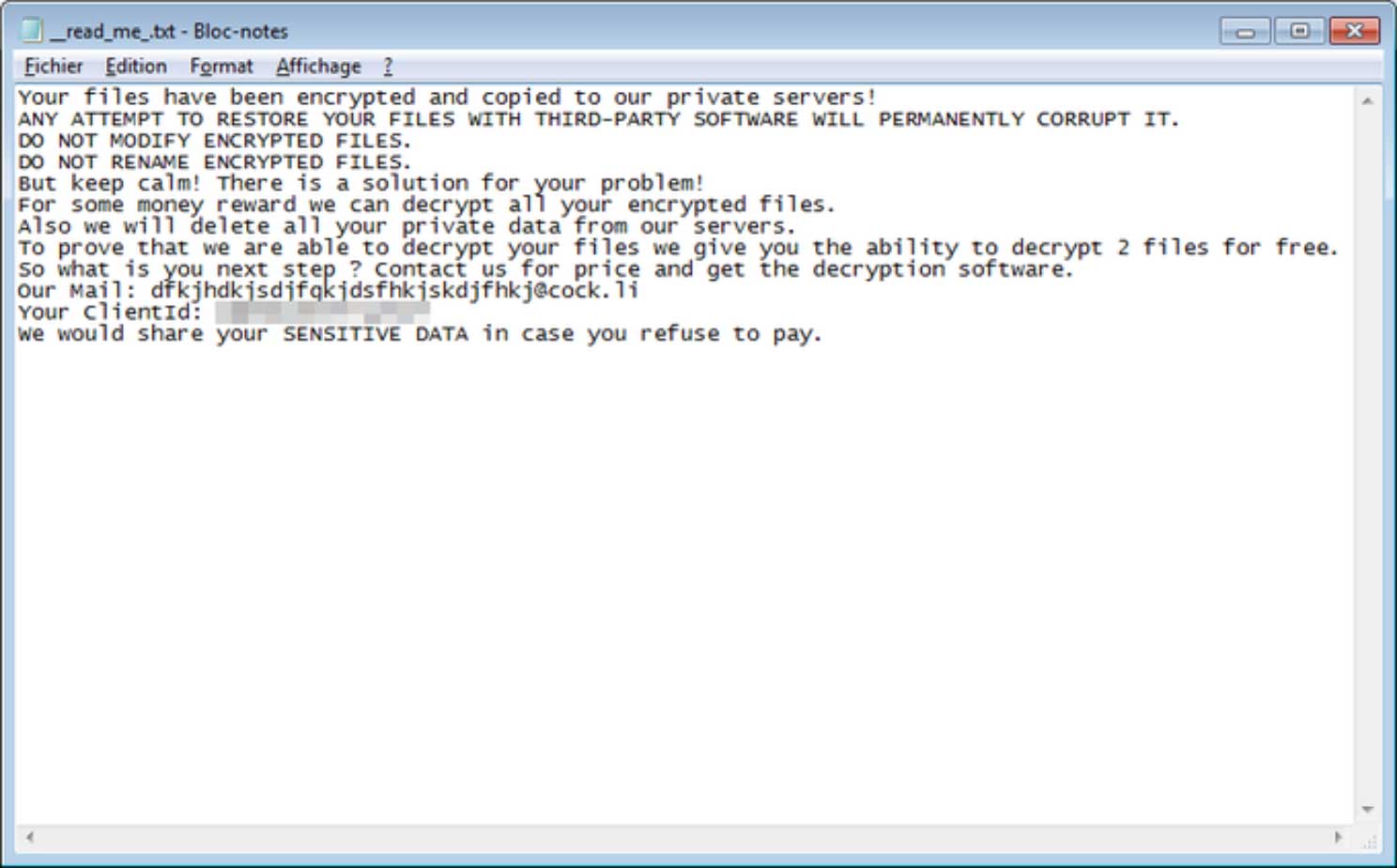
S!ri found a new ransomware that appends the .howareyou extension to encrypted files.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
JAMESWT found a new AgeLocker ELF ransomware (targets QNAP devices) that adds the .kmd suffix to encrypted files.
Two recent ransomware waves that targeted Israeli companies have been traced back to Iranian threat actors.
xiaopao found a new ransomware that appends the .devos extension. This is different than Phobos, which also utilized this extension.
A ransomware group has now started to run Facebook advertisements to pressure victims to pay a ransom.
Office furniture giant Steelcase says that no information was stolen during a Ryuk ransomware attack that forced them to shut down global operations for roughly two weeks.
The DarkSide Ransomware operation claims they are creating a distributed storage system in Iran to store and leak data stolen from victims. To show they mean business, the ransomware gang has deposited $320 thousand on a hacker forum.
Cisco Talos has recently discovered a new version of the CRAT malware family. This version consists of multiple RAT capabilities, additional plugins and a variety of detection-evasion techniques. In the past, CRAT has been attributed to the Lazarus Group, the malicious threat actors behind multiple cyber campaigns, including attacks against the entertainment sector.
Michael Gillespie found a new STOP ransomware variant that appends the .vvoa extension to encrypted files.
Michael Gillespie found a ransomware group known as “LV” utilizing REvil software.