KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







TroubleGrabber, a new credential stealer discovered by Netskope security researchers, spreads via Discord attachments and uses Discord webhooks to deliver stolen information to its operators.
Several threat actors use the new info stealer to target gamers on Discord servers and to steal their passwords and other sensitive information.
Its capabilities are similar to another malware strain dubbed AnarchyGrabber [1, 2, 3] that infects Discord users, also used for harvesting credentials and disabling the victims’ two-factor authentication (2FA).
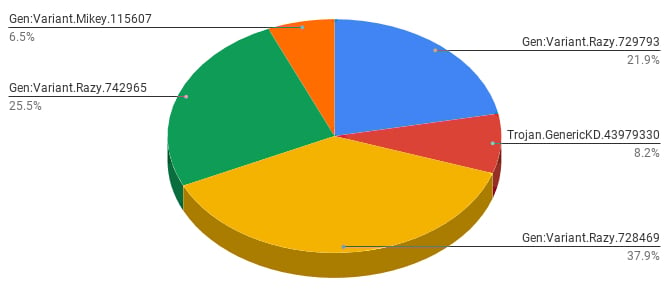
Netskope discovered the info stealer in October 2020 while collecting data for a previous report, with TroubleGrabber samples (detected as Razy variants) making up over 85% of all 1,650 malware samples targeting Discord during October.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
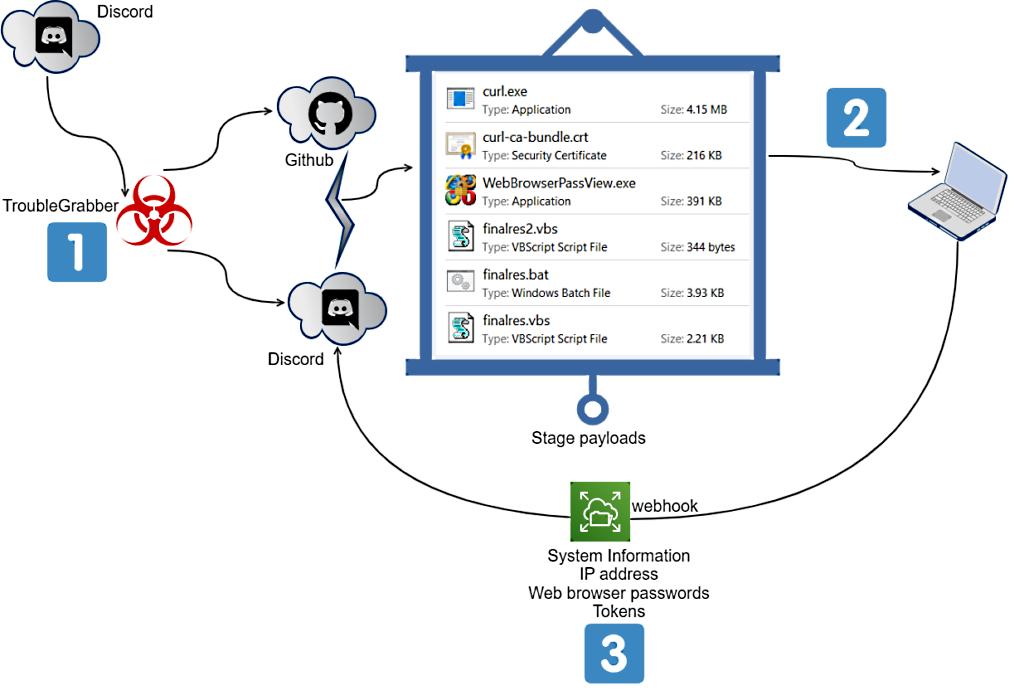
Discord and Github are both used to download next stage payloads to the C:/temp folder once a victim is infected with TroubleGrabber.
The malware also uses Discord webhooks to communicate with its command-and-control (C2) server and to send the victims’ stolen information.
TroubleGrabber steals a wide range of important information including “web browser tokens, Discord webhook tokens, web browser passwords, and system information.”
All this collected information is sent by the malware through chat messages using Discord webhooks to the attackers’ Discord servers.
The malware is created by a threat actor who goes by the name of Itroublve. TroubleGrabber’s author currently runs a Discord server with over 500 members, and hosts next stage payloads and the malware generator’s on their public GitHub account.
Netskope also found that have used a YouTube tutorial on how to use TroubleGrabber to set up their own Discord servers for hosting the malware.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
TroubleGrabber is known for primarily being delivered onto victims’ computers using drive-by downloads via Discord attachment links.
“We identified more than 1,000 generated binaries that were distributed via drive-by download URLs with file names posing as game cheats, Discord installers, and software cracks,” Netskope says.
The malware was distributed via Discord in 97.8% of detected infections, “with small numbers distributed via anonfiles.com and anonymousfiles.io, services that allow users to upload files anonymously and free for generating a public download link.”
In some cases, the info stealer also spread among Discord users from over 700 different Discord server channel IDs.
“Based on the file names and delivery mechanisms, TroubleGrabber is actively being used to target gamers,” Netskope concludes.
Netskope’s Threat Labs shared TroubleGrabber indicators of compromise (IOCs) with Discord, GitHub, YouTube, Facebook, Twitter, and Instagram (whose platforms were used in attacks) on November 10th.